Whoa! Okay—let me be honest up front: I’ve been using Phantom as my go-to Solana browser extension for months now, and it’s earned that spot mostly by being fast, clean, and unobtrusive. My instinct said “this is different” the first time I connected it to a dApp and saw transactions land in under a second. But somethin’ about wallets always keeps me on edge. Seriously? Yes. Wallets are weirdly intimate tech—your keys, your access, your money—and a smooth UX doesn’t erase the risk.
Here’s the thing. Phantom nails the experience for everyday Solana users: account management, SPL token support, collectible previews, staking, and even NFT handling that doesn’t feel clumsy. But initially I thought it was just a prettier interface. Then I dug into the approval flows, permissions model, and signing UX—and that changed my view. On one hand the fewer popups the better; though actually I want clear confirmations. Balancing convenience with security is the whole game here.
So this piece is a practical walkthrough and opinionated guide—what works, what bugs me, and how to use Phantom safely as a browser extension. Expect tips, little tangents, and a few “aha” moments. (Oh, and by the way… I link to the extension download spot later—only one link, as promised.)

Why choose a browser extension wallet on Solana?
Fast network, fast UX. Solana’s throughput makes in-browser transactions feel instantaneous, and that’s appealing when you hop between marketplaces and DeFi apps. Browser extensions sit between your browser and the web app, acting as a gatekeeper for signing requests. They’re not perfect, but they’re the most frictionless way to interact with on-chain apps right now.
My gut said the convenience would breed careless behavior. And yep, I’ve seen people accidentally authorize contracts with broad permissions. Initially I thought “oh that won’t happen to me”—but then I watched a friend approve a token allowance without reading the modal. So here’s a practical checklist: keep one “hot” account for daily use, and another cold account for larger holdings. This separation is super helpful and very very important if you want to reduce blast radius.
Short tip: create multiple Phantom wallets within the extension. Use one for buys, another for staking, and a hardware-backed account for savings. It’s simple and effective.
Installing and setting up Phantom (quick, sensible steps)
Okay, so check this out—installation is straightforward, but small missteps can stick you. First install the extension. If you want to download it from a specific mirror or guide, grab it here. After installation:
- Create a new wallet or restore from seed. Write your recovery phrase on paper—no screenshots, no cloud notes. Seriously, don’t.
- Set a strong password for the extension. This only protects the immediate interface; the seed phrase still matters most.
- Enable connection privacy settings as you prefer, and review permission prompts carefully when dApps request access.
Initially I rushed the restore on a test device and nearly skipped writing the phrase down. Actually, wait—don’t do that. If you lose that phrase, it’s over. No customer support can recover your keys.
Security: what Phantom does well and what it doesn’t
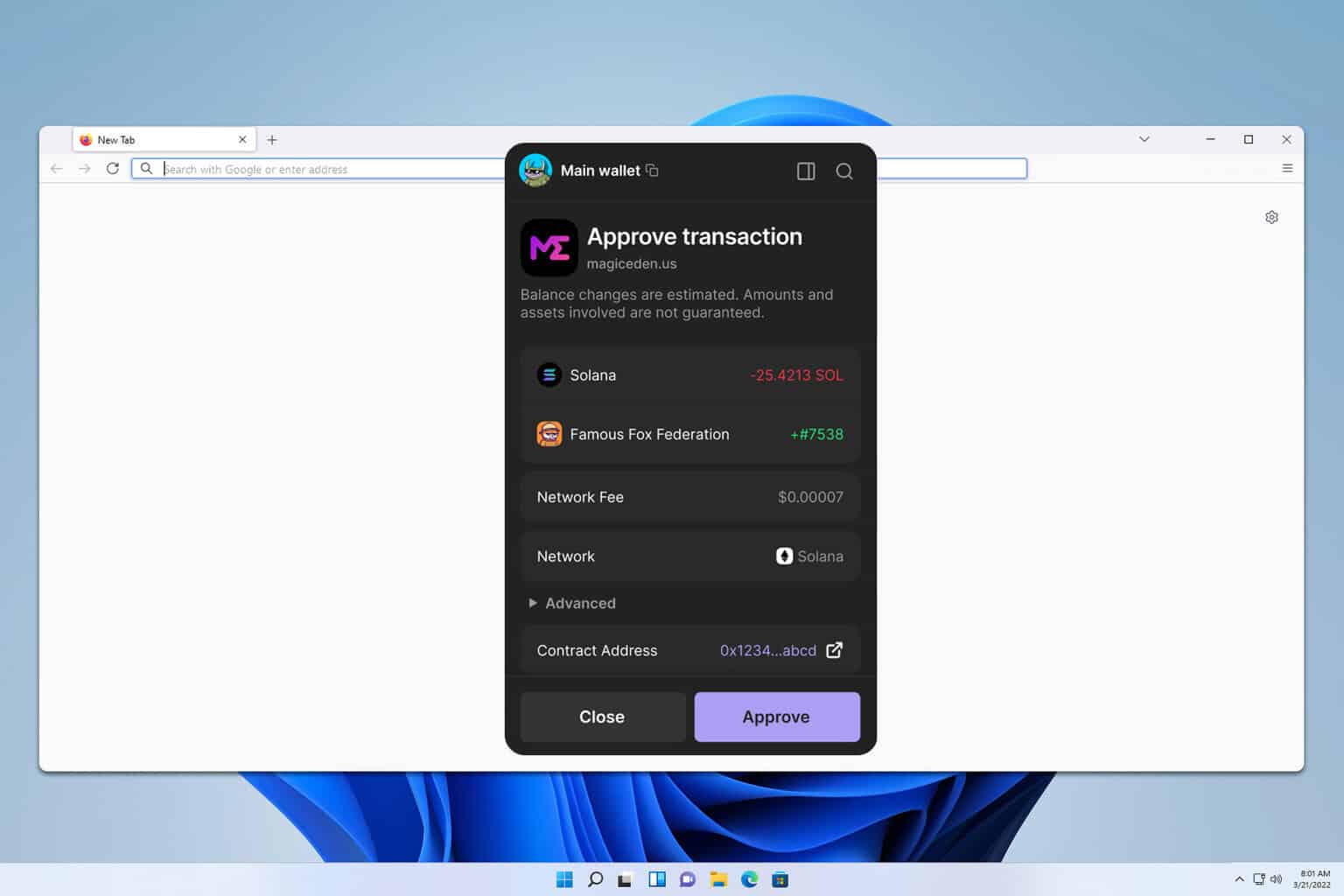
Phantom protects your keys locally, and recent iterations have tightened permission requests and UX around signing. That reduces accidental approvals, though it isn’t foolproof. There’s no substitute for user vigilance: always verify the transaction details, the destination, and the amounts. If something looks odd, cancel and inspect the dApp contract on a block explorer.
One nuance I like: Phantom separates “connect” permissions from “sign” permissions. A site can request to view your address, but signing still requires explicit confirmation for each action. That said, some token allowances are still a gray area. Read the approval modal—if an approval says unlimited allowance, think twice and consider using a smaller allowance or a one-time approval pattern where supported.
Hardware wallets: plug them in. Phantom integrates with Ledger and Trezor (when supported), which gives you that extra layer of protection; the keys never leave the device. I’m biased, but adding a hardware signer for large positions is a small friction for a big security payoff.
UX tips, tricks, and small annoyances
The UX is slick. Really slick. Transaction previews are clear, token images display, and the devtools-friendly logs help when something goes sideways. But here’s what bugs me: some dApps mislabel instructions, and phishing clones sometimes mimic the Phantom modal too well. My advice—compare transaction data with the dApp UI and only accept signatures you understand. If a transaction includes a program you don’t recognize, pause.
Also: Phantom’s in-extension token swaps are convenient, but slippage and liquidity matter. Use small test amounts first. And if you use staking, know that unstaking windows and cool-down periods differ across validators. Read the validator info—validator choice matters for rewards and uptime.
Privacy and metadata
Extensions reveal your addresses to connected sites, which can be tracked across sessions. If privacy matters, rotate addresses and avoid connecting every site to your main account. Mixers and privacy solutions exist but come with legal and reputational complexity. I’m not endorsing anything shady—just noting the trade-offs. Your public addresses are public; treat them like an email you can’t change.
FAQ
Is Phantom safe for NFTs?
Generally yes. It displays media and metadata which is handy. But NFTs often require marketplace interactions; always review the approval scope before signing and use a secondary wallet for active trading to limit risk to your primary holdings.
What if I lose my seed phrase?
There’s no recovery path without it. Phantom cannot restore your wallet. So write it down in multiple secure places and consider a steel backup if you’re storing material value.
Can Phantom be used with hardware wallets?
Yes. Phantom supports hardware integration (like Ledger). Use hardware for high-value accounts and software extension for day-to-day interactions. It’s a best practice I follow.
